![[Go to /]](/DutchGrid-logo-CA.gif)
DCA Root Service
DCA Root CA G1
Trusted Certificate Service TCS
Request your certificate with Academic Login
Guide and tools
Production CA (MS)
Overview
Manage Your Certificates
(for non-TCS users)
Find a local registrar
Classic interface
Help with your request
Host certificate requests
Submit your request
Download your certificate
Renew your certificate
Request revocation
Reliance information
Policy Statement
Reliance Information
NL e-Infra Zero
(training services)
Documentation
Legacy Cert Request Guide
Change a passphrase
RA OpsGuide
OpenSSL for Windows
eToken Guide
Links
EUGridPMA
IGTF
Privacy Policy
|
Certificate Request Walkthrough
Welcome to the DutchGrid CA. For user certificates, the preferred application
processes is to use the fully interactive client tool jGridstart - the GUI based application wizard that will guide you through the
entire process in a few simple and easy steps.
Get your certificate via jGridstart ....
If, for some reason, this tool does not work for you yet for personal
certificates, please get in contact with us to resolve the issue and
meanwhile follow the process detailed below.
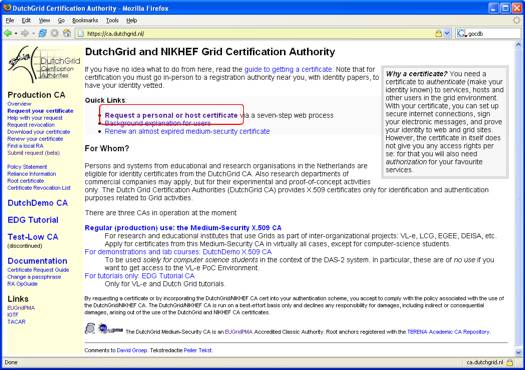
| Start your application process by clicking the Request a personal or host certificate link to go to the web form registration page. |
 |
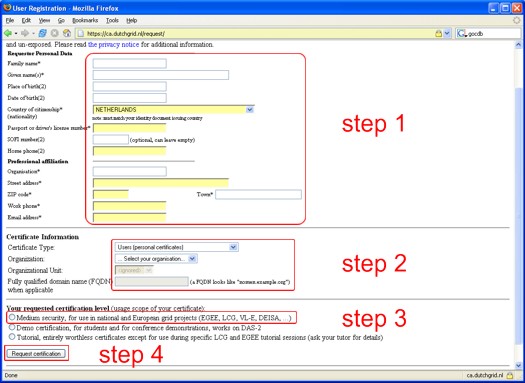
Then, complete the form:
- Please provide your personal details in the form provided (step 1).
If you are requesting a personal certificate, your given name(s)
and your family name (in that order) will be used to construct your
certificate common name.
- Once you've completed your contact details, please select your type of
certificate: "user" or "host", and subsequently select your organisation
(step 2).
Depending on your organisation, you may also have to select your
organisational unit.
If you are requesting a host certificate, you will have to provide the
host name at this point as well. Usually, this is the fully
qualified domain name (FQDN), such as "grid.example.org". In specific
cases (your middleware documentation will say so), you should ask here
for a service certificate, which looks like "ldap/info.example.org".
-
In step 3, select your certification level. In virtually all cases
(unless you're a student trying to use the computer-science-only DAS-2 system)
you should select Medium security at this point.
- When the form is complete, press the Request Certificate button
at the bottom (step 4).
|
 |
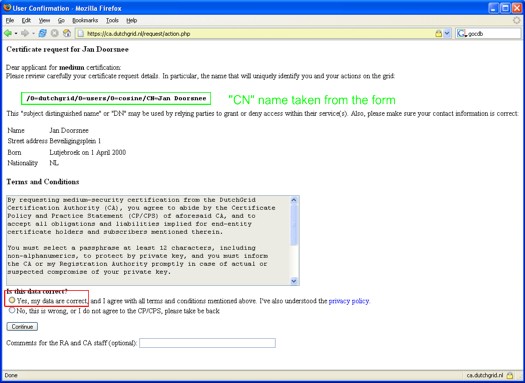
You are now presented with a confirmation screen. Please read through
the acceptable use policy, and if you agree, check the Yes radiobutton
at the bottom. Then, click the Continue button.
|
 |
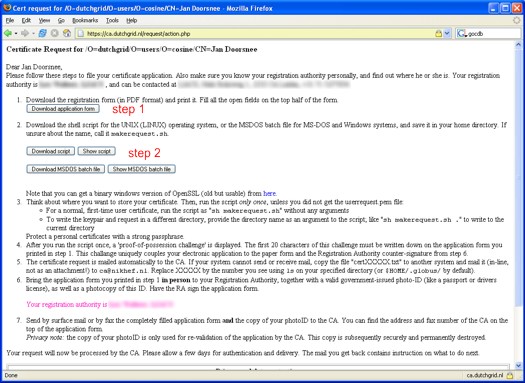
At this point, you get a page with a detailed description of the next
steps. Please read through these carefully, and consider printing
this page for future reference. You should do several things now:
- Download the PDF application form. This PDF file, which has been
partcially filled for you already, you should print on paper and then
complete the top section of the form by hand. You will see a place where
to fill a Proof-of-possession challenge, which you will get
when you run the script from step 2 immediately below.
- Download the request generation script, using any of the buttons of
step 2. There is a version for
Unix and one for MS-DOS and Windows, but if you have the choice please
do use the Unix (Linux) version, as it has a better interface.
You can store the script by downloading it via the browser and saving it
to disk, or by displaying it and copy-pasting the entire script into
an editor on the (Unix) system where you want to get and use your
certificate. The suggested name for this script is makerequest.sh.
On this system, which you must trust and where files will
live for a long period of time, you will generate the key pair
that is associated with your certificate.
|
 |
-
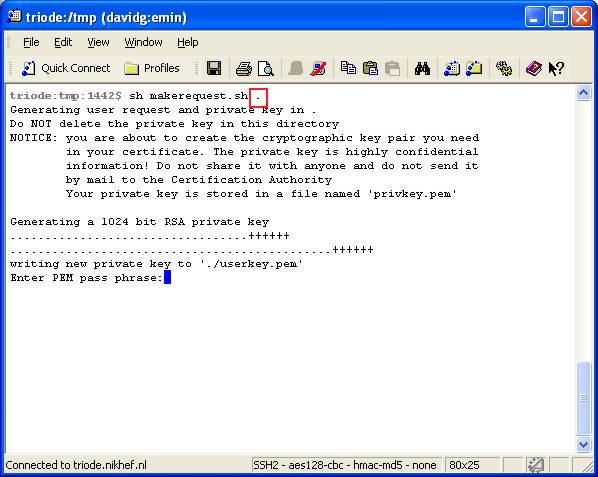
Now, run the script makerequest.sh, from a system prompt.
In order to run the script, you should have openssl in your
path.
This script can be run without any arguments, in which case
the certificate request, and the associates private key will be generated
in the ".globus" subdirectory of your home directory, or - in
case this one already exists - a variant name thereof. However, if you do provide an argument, this argument specifies the directory in which the certificate request and the key pair will be created.
- If you requested a personal certificate, you will now be asked for
a passphrase. This passphrase, just like a normal password, will
be used to protect access to your private key, the piece of private
data that will be used to authenticate you and prove your association
with the certificate.
Remember that your private key should never be disclosed to anyone
but you yourself. Although your certificate is public (it can and will
be sent via email &c), the private key is very private, and if you
give away your key, anyone with that key can impersonate you!
-
Choose a strong passphrase of at least 12 characters, mixing in upper-
and lower case letters, digits and special characters. Only if you are
generating host certificates, you will not have to enter a passphrase,
as the key pairs for these host certificates are only protected with the
simple unix permission scheme (but then, they are bound to only one host).
|
 |
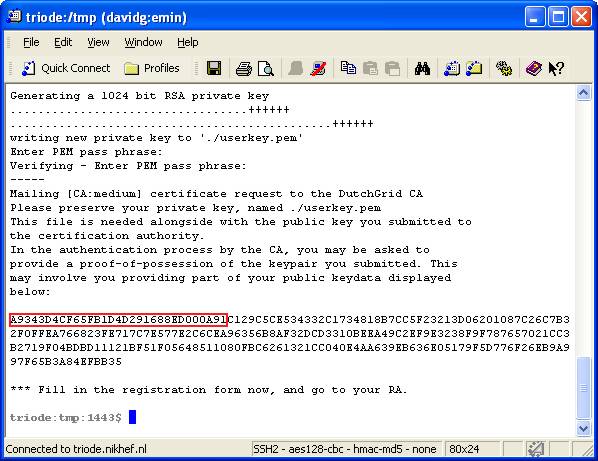
After you provided the passphrase (you have to give it twice to prevent typing
mistakes), the key pair is generated for you and a proof-of-possession
challenge is displayed. Write the first 20 characters of this
challenge on the paper form you printed earlier.
In case you ran this script on a Unix host, it will attempt to send
mail automatically and thus submit your request. If your system
cannot sent email, if your mail is modified in-transit (MacOS), or if you
use an MS-DOS or Windows system, submit the generated request file,
called certreqXXXXXX.txt that has been written to the
directory, via the web upload interface.
|
 |
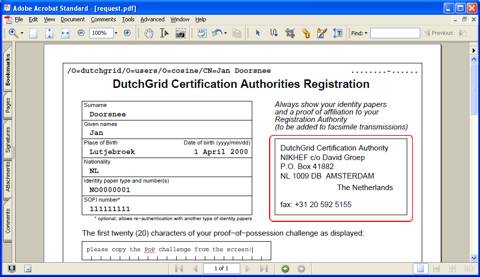
The electronic part of your application is now complete. Take the
paper form to your nearest RA (his or her name is written on the
paper form), and prove your identity to the RA. He or she will then
counter-sign the form and hand it back to you, for mailing or faxing
to the Certification Authority. The address and facsimile number
are printed on the top-right hand corner of the form.
|
 |
|
![[Go to /]](/DutchGrid-logo-CA.gif)






